Cyber Security Blog of Chris Dale
-
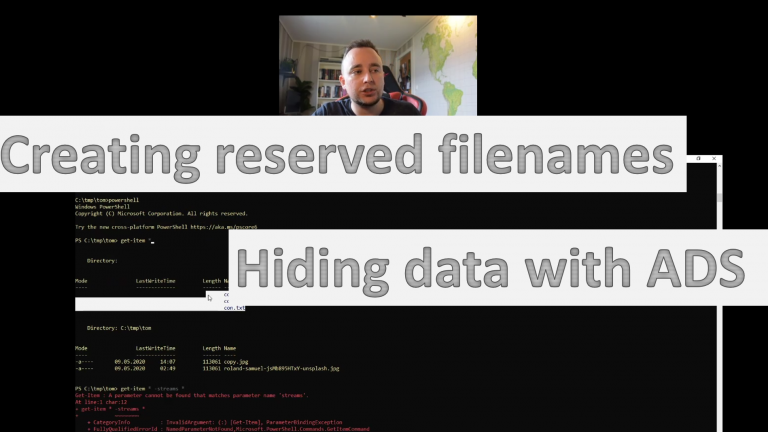
Creating reserved file names and Alternate Data Streams
I created a Youtube video to prove how to create reserved file names using the \\.\ prefix in the command line. Also I show how to append ADS to facilitate hiding and other interesting stuff.
-

Security Misconceptions 2020
Yesterday I did a SANS @Mic talk where I presented on common security misconceptions. The talk discovers many pits and fallacies we make while consulting ourselves and others within information security. I hope it’s interesting! You can find it here:
-

Youtube Series – Bookshelf review
A series on the books on my bookshelf has been completed. You can find all the videos here: https://www.youtube.com/playlist?list=PLag7W-lJE2Aw4m1754iJd3tQlgnr4eAeQ
-

Youtube Series – Web Hacking
I’ve got 27 videos on how to work with web hacking, working through the popular wargame OverTheWire.org, specifically the game called Natas. Check out my videos here: https://www.youtube.com/playlist?list=PLag7W-lJE2Aw8hzezQl17ZlE6CfNS3nYu
-

Gmail alert on senders who might be trying to phish you
I noticed a great new alert today on my GMail account. Previously I’ve received emails from David Cohen on his business email, however he suddenly sent me an email from his private email address. This sparked Gmail to give me an alert, saying that this individual might be pretending to be someone they’re not. Pretty…
-

Netcat backdoor without -e and mimicking Netcat with bash
Netcat backdoor without -e (execute option) Netcat is installed by default on a lot of Linux systems, however we are seeing more and more Netcat’s are compiled without the -e option. The -e options allows us to execute and serve an executable over the connecting socket. It is incredibly handy feature, both for controlling an executable over a network connection,…
-

Smart House Attack Vectors
There’s a very healthy debate going in Norway right now regarding Smart Home security. Internet of Things security is poor, as proved multiple times before by researchers, malware and even worms. Are our devices, and private information safe, just because we got a WPA2-PSK enable WIFI network, and strict firewall rules? In this blog post I’d…
-

Case Study: Breaking into the Smartest Smart Houses
Because media wont be able to cover all the technical details, and also I don’t want to engage in responding to comments on different news sites, I thought I’d rather share my methodology here. Hopefully you’ll take the time to read this story on how I tried to hack this smart house, and perhaps pick…
-
Updating the HackRF One’s firmware
Instructions might be a bit unclear on how to ugrade the HackRF’s firmware, so here’s a short step-by-step guide. Download your appropriate HackRF release: https://github.com/mossmann/hackrf/releases/ Extract: tar -xfv hackrf-2017.02.1.tar.xz Open up the folder containing the firmware: cd hackrf-2017.02.1/firmware-bin/ Update the SPI flash: hackrf_spiflash -w hackrf_one_usb.bin Update the CPLD: hackrf_cpldjtag -x hackrf_cpld_default.xsvf Press the reset button and let it…
-

Audio reminder for when computer is back online
This handy little command reminds me by audio when my computer is back online. I just had a 30 minute Internett outage, and it was nice to get right back to my seat when my computer started bleeping out alarms. for /l %i in (1,0,2) do @ping -n 2 8.8.8.8 2>1>nul && @powershell -command [System.console]::Beep(300,1000)…
Looking to get in touch?