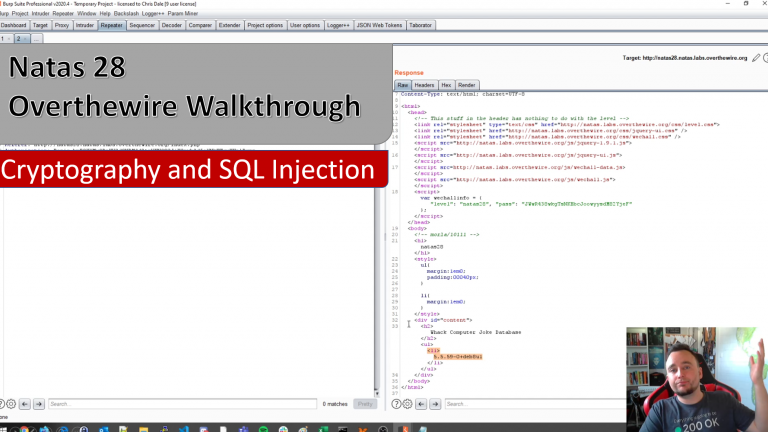
Cryptography is not always deployed in a secure manner. When user controlled input is provided to a server and the server encrypts the data, outputting the results back to the user, it might be used as an oracle to learn which plain-text provide which encrypted data. This weakness is often present in Electronic Code Book chipers.
YouTube video release – Breaking ECB Crypto (No programming)
by